Disabling TLS 1.0, 1.1 and 1.2 in Windows server and allow only the TLS 1.3 version.
You may be facing some vulnerability issues with your IIS hosted websites related to TLS. Especially when doing a penetration test you may see reports such like such like “TLS/SSl Weak Message Authentication code Cipher Suites” with solution statement saying “Disable any weak HMAC algorithms within the TLS Configuration”.
Even if you are not facing any such issue it is recommended that you need to disable TLS 1.0 and 1.1 at least to grade your SSL security to a top level. Here are the steps how you can disable TLS 1.0 and 1.1 but of course if need TLS 1.2 (although it is widespread protocol).
Before starting you may need to check what are the protocols enabled/supported in your system. The best and quickest way to check is using an online tool (Ex: https://www.ssllabs.com/ssltest/ ).
Assume you have all 4 protocols (TLS 1.0, 1.1, 1.2 and 1.3) enabled and we now going to disable TLS 1.0 and 1.1.
- Open your registry by typing Regedit in your run command.
- Go to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols
- You may already see that TLS keys and Server keys under them are created. You may see none or for some protocols. Don’t worry if you don’t see them, we can create them.
- Let’s assume there is no keys already there related to TLS protocols hence let’s create them.
- Add a key under Protocols and Name it as TLS 1.0
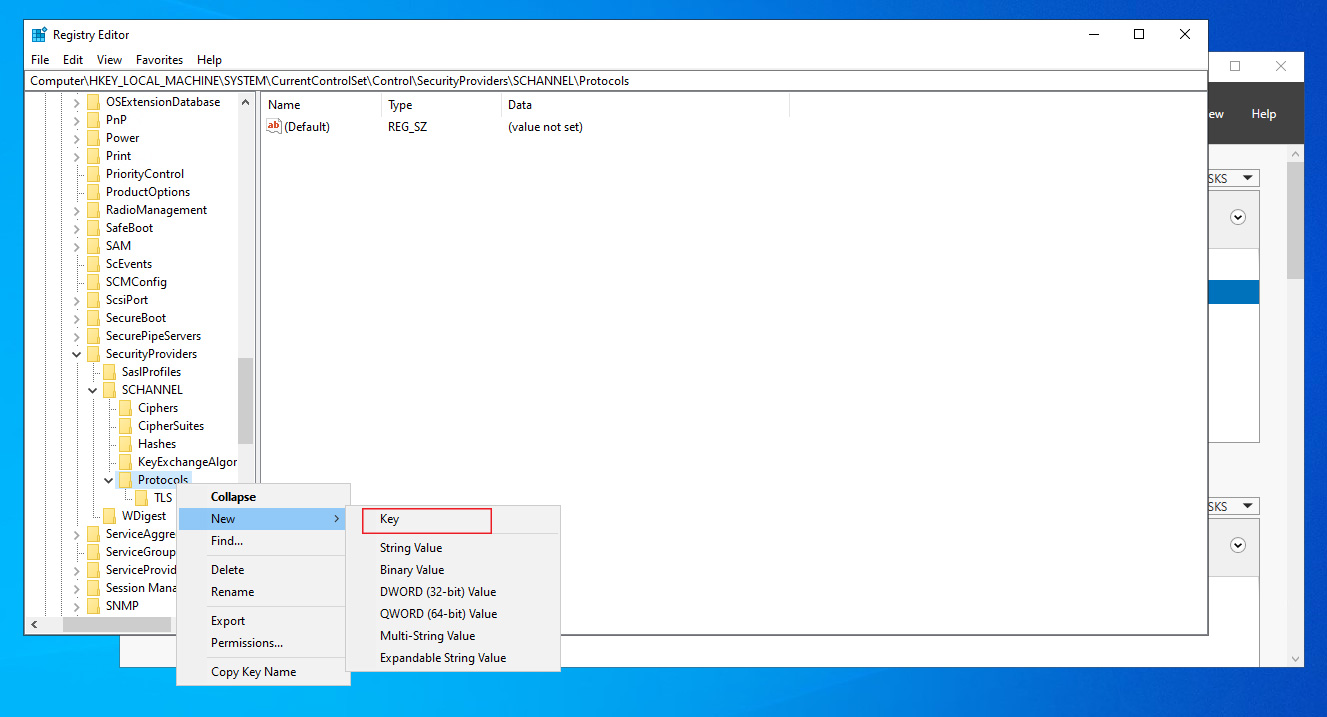
- Add another key under the TLS 1.0 and name it as Server
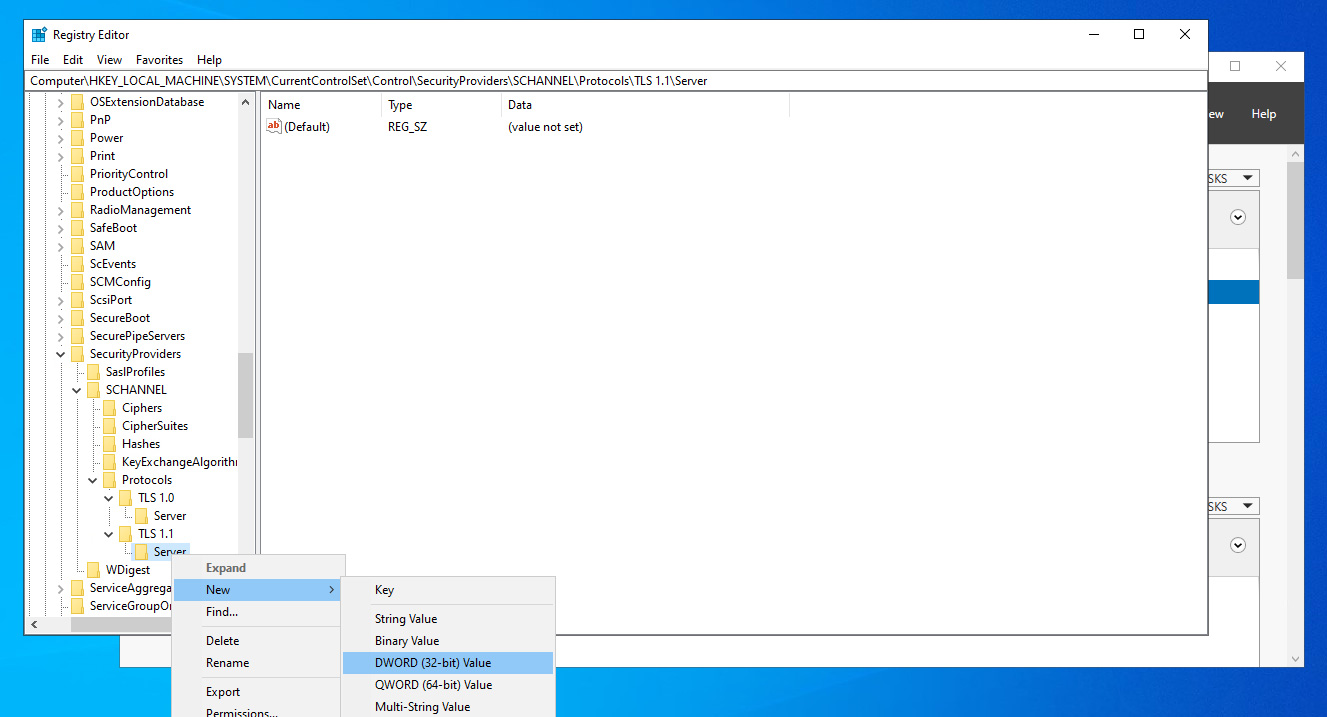
- Now add a new Dword under the Server key and name Dword as Enabled.
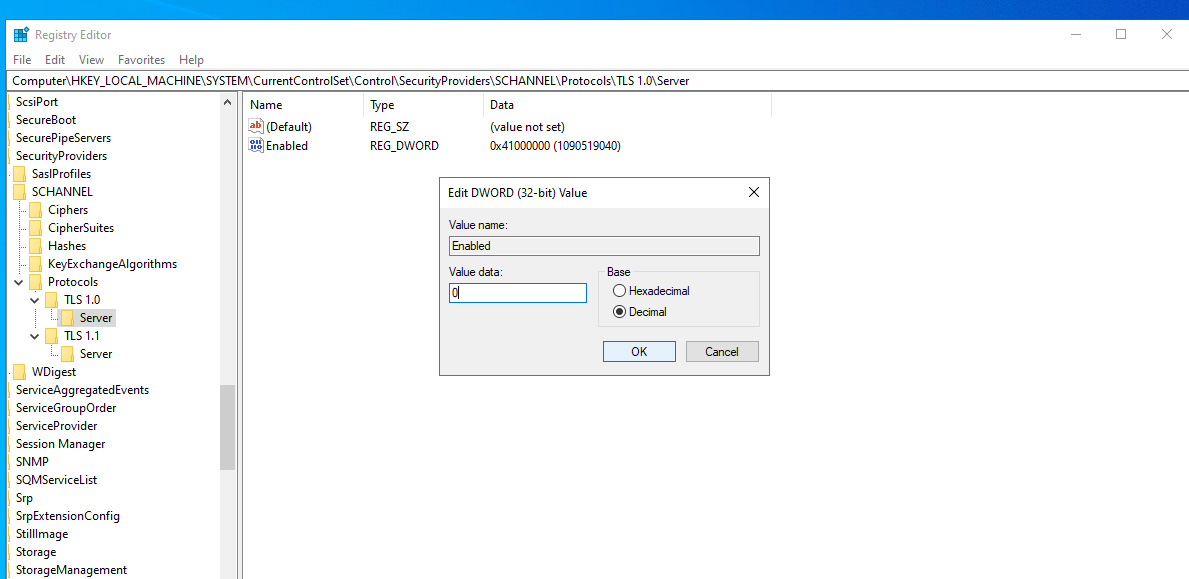
- Now change the value of the new Dword (Enabled) to 0 as like the image below.
- Just repeat the same steps for the other TLS protocols example TLS 1.1.
- Once you disabled all desired protocols, make a complete restart to take them effect.
